🧪 Deep Dive: What a Virus Scan Reveals About Impact.GG RSPS Client
Impact.GG Security Scan - Community Concerns Validated by Open-Source Analysis
For weeks, players have hesitated to launch Impact.GG, fearing that its client might pilfer browser cookies or worse. RuneList.io obtained a third-party Falcon Sandbox report on Impact.jar; the publicly available forensic data paints a worrying picture. This forensic scan can be read in full here.
🔍 Key Concerning Behaviours
-
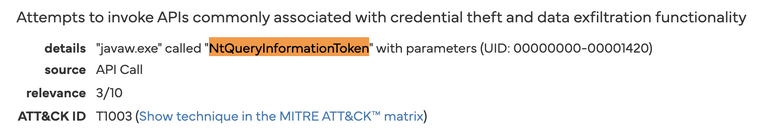
OS Credential Dumping API. The client invokes
NtQueryInformationToken(MITRE T1003) to pull the user’s logon token — the first step in decrypting DPAPI-protected Chrome/Edge cookies. -
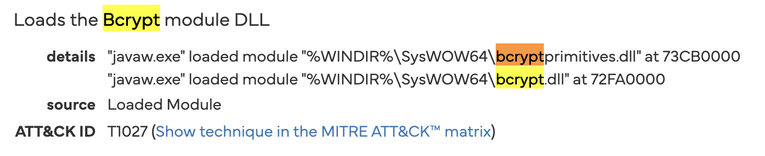
Crypto Primitives Loaded.
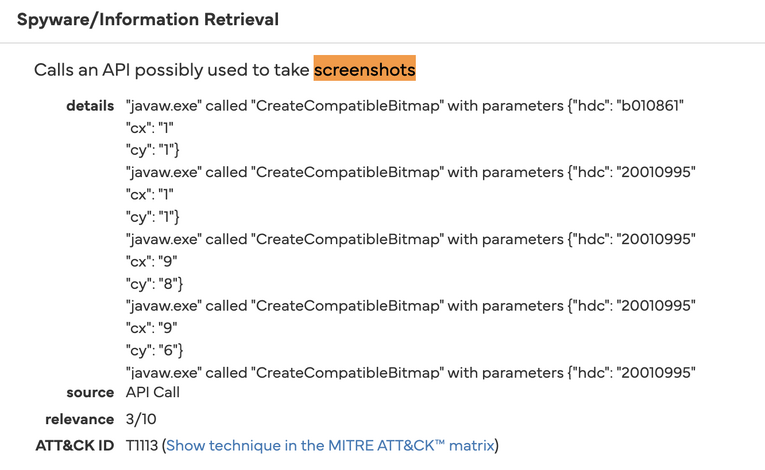
bcrypt.dllandbcryptprimitives.dllare sideloaded byjavaw.exe, giving the jar the exact AES routines required to turn cookie blobs back into plaintext. - Screen-Capture Capability. Falcon flags ATT&CK technique T1113; three screenshots were snapped during analysis, showing the client can read the desktop buffer — functionality no RSPS launcher legitimately needs.
-
Encrypted Payloads Dropped. A 1 MB high-entropy file,
codebase25.dat, is written to%APPDATA%\Impact AppData, a classic stash location for harvested credentials. -
Cookie-Cache Artefacts. Additional blobs like
client-sha1.datappear in the same folder during runtime, implying a rolling cache of stolen data. -
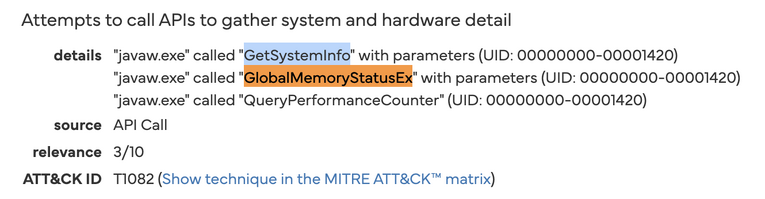
Host Reconnaissance. Calls to
GetSystemInfoandGlobalMemoryStatusExprofile hardware before payload execution - overkill for simply launching an RSPS.
🍪 How the Client Could Steal Browser Cookies
Modern browsers encrypt session cookies with DPAPI, but any process that can obtain the user’s logon token and load Windows crypto libraries can silently decrypt them. NtQueryInformationToken supplies that token, while bcrypt.dll exposes the AES routines used by Chrome and Edge. Taken together, these two calls give Impact.jar everything it needs to lift persistent login cookies - a capability extraordinarily unusual for an RSPS launcher.
📸 Why the Screenshot Flag Matters
ATT&CK technique T1113 marks software that captures the screen buffer. In the sample run, Falcon generated three distinct screenshots from javaw.exe, proving the client can view whatever is on your desktop — credentials, wallet QR codes, or streaming overlays. Legitimate RSPS clients rarely, if ever, need this permission.
🛡️ Safe-Launch Checklist
- Run the jar in a disposable VM or sandbox.
- Use throw-away credentials; never log in with your main OSRS account.
- Keep crypto wallets and password managers closed while testing.
- Monitor outbound network traffic for silent TLS beacons.
- Wait for a reproducible, signed build or a full source-code release before trusting future versions.
📝 Sources for these findings
- The open-source security scan was performed by Hybrid Analysis and can be found here: https://www.hybrid-analysis.com/sample/620cbe7fb21181a620790b32cbc53d19de63d79f8a0a9a39edf7877d3b5664a5/68386d8b8d600d749f0d3aac
Attempts to invoke APIs commonly associated with credential theft and data exfiltration functionality
Loads the Bcrypt module DLL
Calls an API possibly used to take screenshots
Attempts to call APIs to gather system and hardware detail
-------------------------
Have insider information about this or any other RSPS story? Message chanston_runelist on Discord. Confidential tips keep the community informed.



.thumb.png.fb770e0fc43721c443976820a7444087.png)
0 Comments
Recommended Comments
There are no comments to display.